
Factors for successful information security management
The term security awareness is frequently used when talking about information security, and rightfully so.
Läs vår blogg, senaste nyheter och ta del av guider och mallar.
Bli inspirerad och öka din kunskap!

The term security awareness is frequently used when talking about information security, and rightfully so.

Blockchain has been described as the technology that can revolutionize the world economy and transform society.

Personal Cloud space is getting very common and soon it will become a necessity rather than a luxury. More on the blog:

Smart Contracts & Blockchain: How can you benefit from adopting Blockchain solutions? More on the blog today:
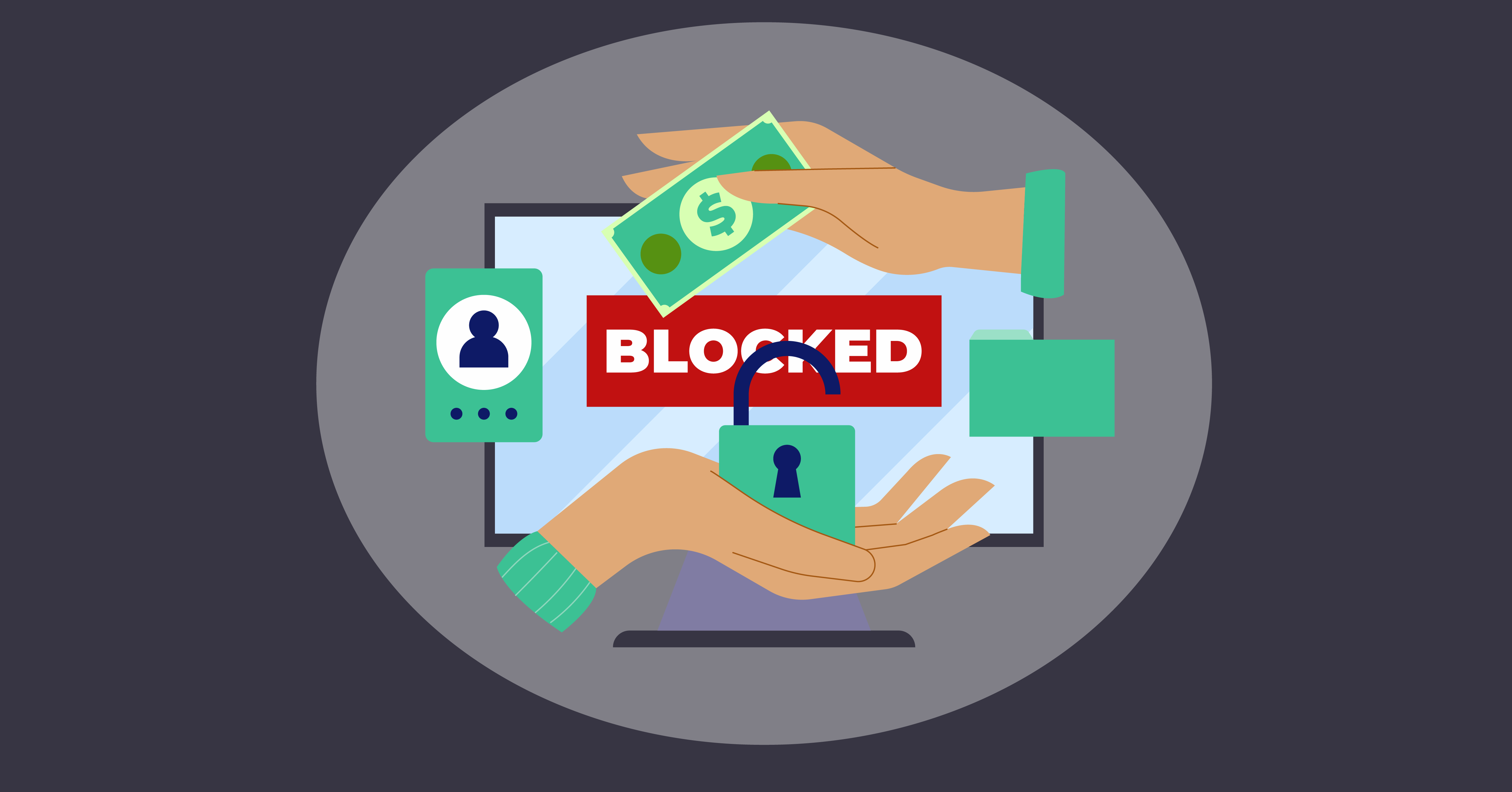
Ransomware is a malicious program that locks down a user to gain access to their information/data by locking the hard disk

Being able to assess risk is a crucial part of life and very important when working with information security.
The journey towards PCI compliance is not always straightforward. The PCI compliance process can be costly and requires a lot of resources

Applications facilitate communication and help us in different ways, in our day-to-day lives. More on the blog

As usual, preparation starts with defining how an ATM works in practice and what the critical components and interfaces are

The objective for both standards is to secure and manage company information, but they do so in different ways and to different extents.

If you’re a small to medium sized business do you have to meet as many requirements and jump through as many hoops as a large enterprise?

Outsourcing operations to a third party means that you share responsibility for reaching the requirements in PCI DSS. Read the our blog now.